MFA Requirements for Cyber Insurance: What Business Leaders Need Now
As cyber‑insurance premiums continue to rise, it’s no longer enough to just “have MFA.” Insurers now demand strong, phishing‑resistant implementations—or they won’t provide coverage. Meeting the mfa requirements for cyber insurance means understanding which MFA types are accepted, how to upgrade legacy systems, and what it means for policy costs and risk.
Why Insurers Are Raising the Bar
MFA is now one of the top technical requirements insurers look at when assessing cyber-risk. Insurance carriers have seen an increase in claims tied to account takeovers, many of which succeeded because the organization relied on outdated MFA like SMS codes. As a result, insurance underwriters are demanding stronger controls across the board.
Understanding Phishing‑Resistant MFA
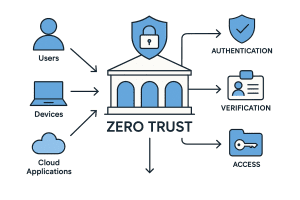
Not all MFA is created equal. Traditional methods—like SMS or mobile app prompts—can be intercepted or spoofed. “Phishing-resistant MFA” refers to methods that verify the user and device in a cryptographically secure way. Examples include hardware security keys (like YubiKeys) and certificate-based authentication. These methods drastically reduce the risk of credential phishing attacks.
Business Risks of Weak MFA
- Policy denial or voiding: Insurers may reject your claim if your MFA does not meet their underwriting criteria.
- Higher premiums: Basic MFA often leads to increased costs. Some insurers offer reduced rates for phishing-resistant MFA adoption.
- Regulatory exposure: Financial and healthcare regulators increasingly expect strong authentication methods as part of compliance obligations.
Five Steps for Business Leaders
1. Audit Your Current MFA
Identify how users are authenticating. Are you using SMS, push notifications, app-based codes, or security keys? Review login methods across email, VPN, remote access, and internal applications.
2. Upgrade to Phishing‑Resistant Methods
Start with your most privileged accounts—executives, finance, and IT administrators. Implement FIDO2-based hardware tokens or certificate-backed smart cards that validate both user identity and device integrity.
3. Confirm Requirements with Your Insurance Provider
Talk directly with your broker or carrier. Ask for a list of MFA methods that meet current underwriting standards and get confirmation in writing where possible.
4. Train Your Staff
Phishing-resistant MFA only works if it’s understood and used correctly. Provide step-by-step training for security key use and make adoption easy across departments.
5. Monitor and Report Compliance
Keep records of your MFA rollout, including coverage by user group and authentication method. This information may be required during insurance renewals or audits.
Helpful Resources
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) offers guidance on phishing-resistant MFA. Learn more from their official publication here:
Implementing Phishing-Resistant MFA (CISA).
Where Cost+ Can Help
Cost+ helps businesses meet the latest Security+ standards required by insurers. We assess existing MFA, implement compliant solutions, and document everything to help you secure coverage at the best possible rate.
Bottom Line
If your company still relies on SMS or app-based MFA, it may no longer meet mfa requirements for cyber insurance. Upgrading to phishing-resistant MFA isn’t just smart—it could be essential to keeping your business protected and insured.
By Thomas McDonald
Vice President