Traditional perimeter-based security models—like firewalls and VPNs—are no longer sufficient in today’s digital landscape. Organizations now rely on cloud apps, remote work setups, and extended third-party ecosystems, rendering old security strategies ineffective. This Zero Trust architecture guide is designed for business leaders, providing clarity on what Zero Trust means, why it matters, and how to implement it successfully.
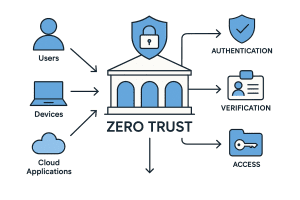
What Is Zero Trust?
Zero Trust is a security philosophy that rejects implicit trust. Instead, every access request—whether from inside or outside the network—must be continuously authenticated, authorized, and monitored. Unlike traditional perimeter defenses, Zero Trust shifts protection to the identity, device, and data layers. The NIST Zero Trust Architecture guide outlines this strategy in detail.
Why It Matters Now
- Remote and hybrid workforce: Employees are using diverse devices and networks, far beyond corporate boundaries.
- Rising cyber threats: Ransomware, business email compromise, and supply chain attacks exploit trust in internal systems.
- Compliance demands: Regulations increasingly mandate least-privileged access and continuous verification.
Core Principles of Zero Trust
- Identity: Strong authentication using single sign-on (SSO), multi-factor authentication (MFA), and identity governance.
- Device Security: Ensuring only trusted, compliant devices can connect.
- Least‑Privilege Access: Granting users only the permissions they need—no more.
- Microsegmentation: Dividing networks into zones so breaches are contained.
- Continuous Monitoring: Ongoing auditing and real-time analysis of access events.
Business Use Cases & Scenarios
- Remote Access: Zero Trust Network Access (ZTNA) replaces traditional VPNs for secure remote work.
- Vendor Collaboration: Grant external users limited, conditional access to sensitive systems.
- Cloud App Security: Enforce identity-based controls on SaaS apps and APIs.
- Regulated Industries: Detailed access records meet PCI-DSS, HIPAA, and financial compliance standards.
Roadmap to Zero Trust Implementation
- Start with an Assessment: Use a maturity framework such as the CISA Zero Trust Maturity Model to evaluate your organization’s current position.
- Establish Quick Wins: Start with high-impact basics: enforce MFA, enable device compliance, deploy SSO, and pilot ZTNA.
- Define Your Access Policies: Create granular rules specifying who can access what resources, under which conditions.
- Roll Out in Phases:
- Phase 1: Identity and device verification
- Phase 2: Network segmentation and application control
- Phase 3: Monitoring, database protection, and automation
- Track Progress with Metrics: Monitor improvements in blocked breaches, abnormal access attempts, and policy compliance.
- Maintain and Adapt: Zero Trust isn’t a one-time project. Policies, tools, and reviews must evolve with threats and business growth.
Technology & Tool Landscape
Zero Trust requires integrated layers of protection:
- IAM platforms: Okta, Microsoft Entra
- MFA solutions: FIDO2 keys, app-based authenticators
- ZTNA gateways: Cloudflare, Palo Alto Prisma
- Microsegmentation tools: VMware NSX, Illumio
- SIEM platforms: Splunk, Azure Sentinel
Select solutions that integrate with your identity, cloud, and endpoint architecture.
Common Pitfalls & How to Avoid Them
- Treating Zero Trust as a product instead of a long-term strategy
- Lacking policy clarity before implementation
- Ignoring employee experience and adoption barriers
- Failing to update protections as new risks emerge
Where Cost+ Fits In
Cost+ helps businesses implement Zero Trust principles through tailored services:
- Support+ – IT help desk and infrastructure support
- Security+ – Endpoint protection, monitoring, and email security
- Compliance+ – Consulting to meet HIPAA, SOX, PCI, and other mandates
Our team aligns Zero Trust adoption with your risk profile and business goals.
Conclusion
Zero Trust is no longer optional—it’s foundational to securing modern organizations. By adopting a strategy that includes strong identity, device validation, segmentation, and continuous monitoring, business leaders can dramatically reduce risk and improve resilience. Use this zero trust architecture guide to assess your readiness, implement smart protections, and create a more secure future for your organization.
By Gregory McDonald